
What is GSMA FS.11? Testing for SS7 vulnerabilities
What is GSMA FS.11? Testing for SS7 vulnerabilities
The SS7 network signalling protocol stack was designed to enable roaming and is still an essential interconnect component for 3G/4G/5G compatibility. However, it has well-known security flaws. GSMA FS.11 (SS7 Interconnect Security Monitoring and Firewall Guidelines) outline the SS7 threats that MNOs should be monitoring. Does your SS7 monitoring stack up?
GSMA FS.11 was the first set of guidelines approved by the GSMA back in November 2015 and has been updated regularly ever since. GSMA FS.11 (SS7 Interconnect Security Monitoring and Firewall Guidelines) outlines at a high level how mobile network operators (MNOs) can monitor and sample SS7 MAP and CAMEL traffic to monitor unwanted or malicious SS7 traffic, and set firewall policies to improve the protection of their networks.
The interconnection network is a private network that connects operators around the world. It enables calls, data and many other services across network and country borders – essentially, roaming.
SS7 – the weakest link
The first roaming case occurred in the Nordics in 1981, but quickly expanded across territories. This was at a time when most operators were state-owned and the partners involved trusted one another. As a result, the SS7 network signalling protocol stack was not designed with security in mind, and is known for its vulnerability to security threats, attacks and hacks.
As mobile operators have continued to add more functions and services, signalling networks are required to carry increasing amounts of sensitive and confidential data, including location, SMS texts, billing data, and so on. This data is sent via roaming interconnectors, which means potentially that anyone with access to the SS7 network can mine the data of any individual on any network in the world.
SS7 attacks can lead to:
- Stolen subscriber information
- Network information disclosure
- Subscriber traffic interception
- Fraud
- Denial of service
Furthermore, to ensure that roaming remains available to users (and remains a significant revenue stream for MNOs) it’s important that there is forward/backward-compatibility between network generations. To provide that interconnect, and continued roaming capabilities, the telecoms industry has worked together to design various messaging protocols – SS7 for 3G CAMEL , DIAMETER for 4G LTE and HTTP/2 for 5G.
GSMA FS.11 outlines Category 1 to 3 SS7 vulnerabilities
However, these points of interconnect represent weak spots, with SS7 (3GSM MAP and CAMEL traffic) notorious for its lack of in-built security, requiring on-going monitoring and protection. Due to backwards-compatibility requirements, it also means that even 5G networks indirectly inherit SS7’s security flaws.
The GSMA’s FS.11 guidelines specifically outline the SS7 vulnerabilities that operators must recognise and protect against, while offering guidelines on where to monitor, how to monitor and how to protect networks.
FS.11 divides SS7 attacks into three categories, as outlined below:
Category 1 – Prohibited Interconnect Packets
- CAMEL packets
Category 2 – Unauthorised Packets
- Addressing Mismatches for Home Subscribers and Inbound Roamers
- Traffic not from Roaming Partners
- Sub-Classification of Category 2 Messages
- Spoofed Traffic to Inbound Roamers
Category 3 – Suspicious Location Packets
- Location Correlation
- Additional Addressing Correlation
- Traffic not from Roaming Partners
- CAMEL Packets
- Sub-Classification of Category 3 Messages
- Dealing with Traffic trying to bypass Category 3 protection
Category 3 type attacks are those that require on-going and continuous “cat and mouse” security upgrades as attackers become more sophisticated and continuously push the boundaries of these types of attacks.
SS7 monitoring at multiple nodes
A common line of defence against SS7 attacks is a firewall. An increasing number of operators are deploying an SS7 firewall, which analyses all signalling traffic at the network border and monitors for all types of known SS7 threats. Firewalls are constantly updated to ensure that they recognise new threats. Of course, the next challenge is to ensure that these firewalls are working correctly.
But to ensure SS7 protection, FS.11 recommends that monitoring is performed at all nodes that receive interconnect traffic, including the following:
- An SS7 firewall (considered to be any node capable of executing SS7 firewalling functionality)
- Gateway STPs (Signal Transfer Points)
- Nodes that send/receive interconnect traffic (MSC Mobile Switching Centre, SGSN Serving GPRS Support Node, HLR Home Location Register, VLR Visited Location Register etc.)
- SMS firewall/home routing nodes
- Network probes/monitoring systems
- Or any other network element, passive or active that encounters interconnect SS7 traffic.
Monitoring by nodes such as STPs, SS7 firewalls and network probes at appropriate points throughout the network provides a wider viewpoint of SS7 activity, while monitoring by nodes such as HLCs or MSCs provides insight into the specific traffic they transport. The goal of monitoring is to gauge whether suspicious/malicious SS7 activity is occurring. How can MNOs ensure this?
Emblasoft’s Evolver testing platform enables full support for FS.11 guidelines
Emblasoft Evolver is a comprehensive platform of test and validation solutions that fully supports FS.11 guidelines. Our service can accurately simulate suspicious SS7 traffic from any emulated node in the network. It can also provide reports on whether firewalls and security functions are operating at their full potential and, if not, identify new threats and highlight where the firewall needs updating.
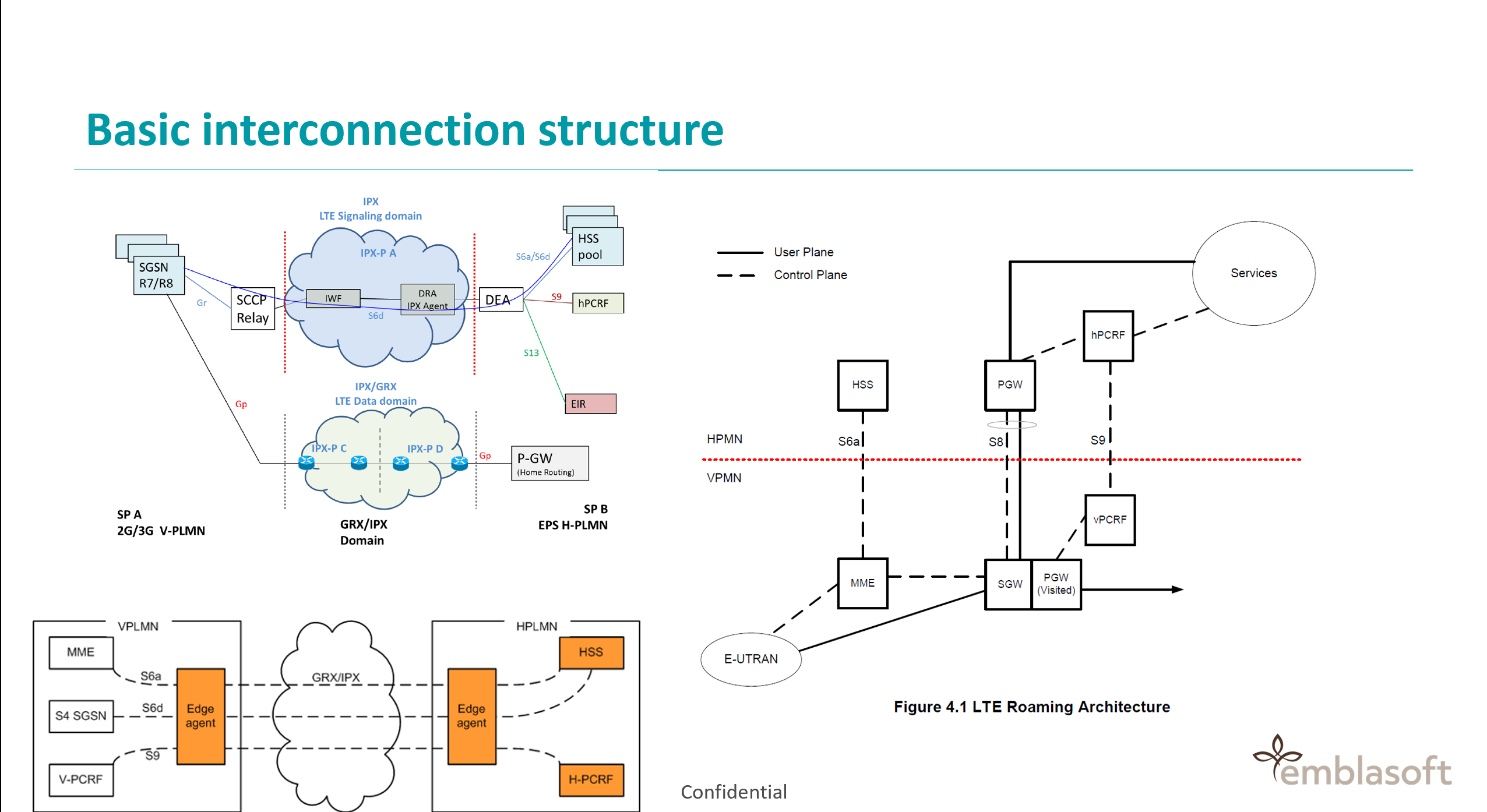
We can simulate all types of traffic listed in GSMA’s FS.11 Categories 1–3, enabling operators to run automated, customised tests against their firewalls or other SS7 defences to identify weaknesses and gaps, and help them to develop robust defences against SS7 attacks.
Evolver provides automated one-off, periodic or active monitoring to provide a clear picture of SS7 vulnerabilities and firewall performance. Our testing solutions can generate and simulate any relevant SS7 messaging and traffic, traffic patterns and suspicious activities. By doing so, our solutions can ensure the validity of all your SS7 firewalls and defences.
The solution is highly flexible. Each of the defined FS.11 threats can be modelled using any network traffic parameters, as well as monitoring for new and unexpected threats as they emerge.
Our active monitoring tools look for known and new SS7 attacks or suspicious traffic on a continuous basis to ensure support for FS.11 guidelines. Our tools can also meet guidelines for Diameter (GSMA FS.19) and other security protocols. Contact us to find out more.